My Key Takeaways: The Surge in Ransomware Attacks Highlighting the Colonial Pipeline Attack

Hello everyone! While doing my research on the recent ransomware attacks that led to sabotaging critical infrastructures, I landed on the colonial pipeline attack. These are my observations and takeaways after analyzing the incident response and the impact of the attack on the organization as well as the general public.
Brief Introduction and Timeline
A surge in ransomware attacks has been observed over the past year in various industries like healthcare, commerce, and finance. Check Point Research reported in March 2021 that ransomware attacks have seen a 57% increase since the beginning of 2021 amid the disclosure of the Microsoft Exchange vulnerabilities. Colonial Pipeline, a major US fuel company, was the victim of such an attack. The Colonial Pipeline, which connects Texas and New York, is the USA’s largest pipeline system, transporting about 3 million barrels of refined oil products per day. It provides over half of the gasoline and jet fuel used by a variety of industries and supports a population of 50 million on the East Coast. Hence when the ransomware attack occurred, it affected this critical infrastructure. Let’s take a look at the timeline of the Colonial Pipeline Ransomware Attack.
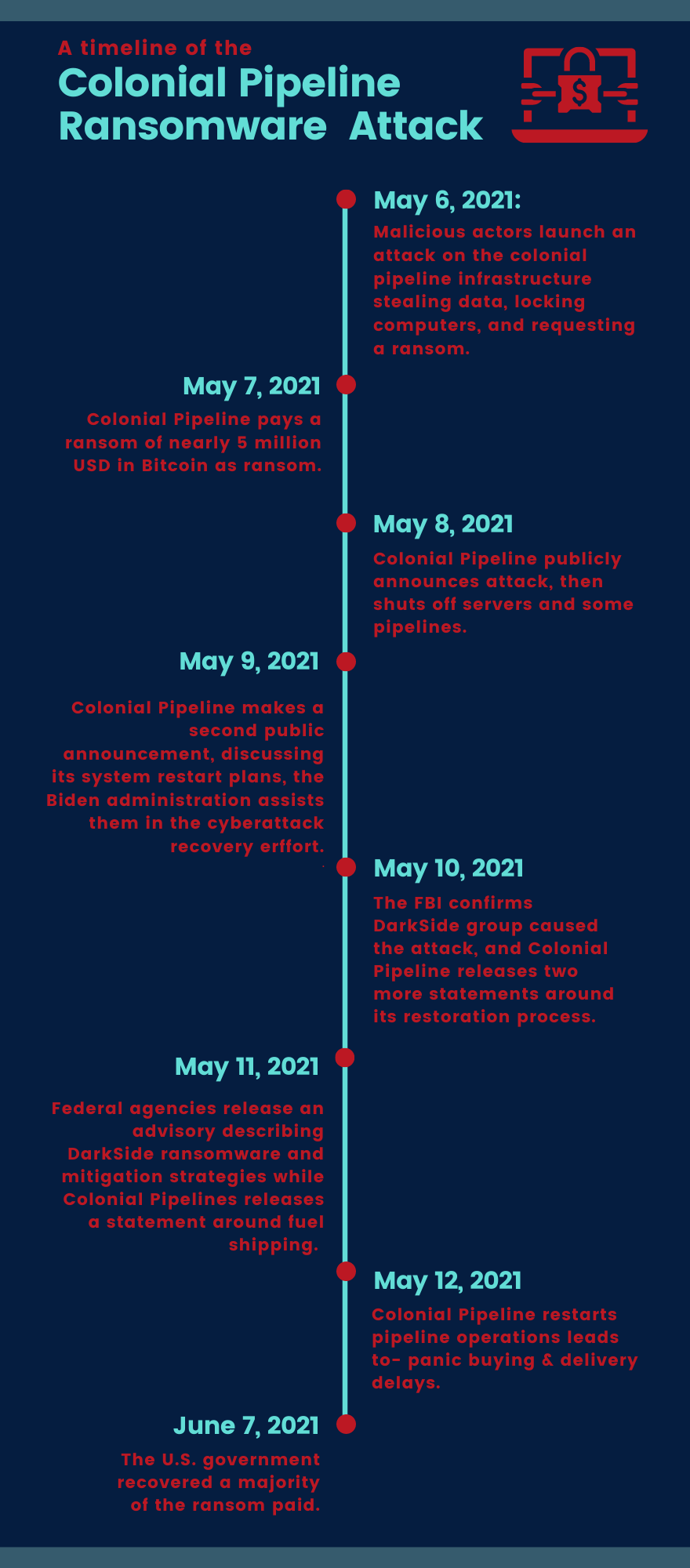
Key Takeaways
Importance of multi-layer authentication & Password Management
In the Colonial Pipeline attack, the attackers exploited a VPN (virtual private network ) functionality that had a single layer authentication mechanism- a password. Although according to the CEO Joseph Blount, it was not a simple or default password. The 2021 “Data Breach Investigations Report” (DBIR) by Verizon highlighted that a majority (61%) of breaches were attributed to leveraged credentials.
After breaking into the infrastructure through this endpoint, the attackers establish a foothold in the network to perform further attacks and to breach confidential data that will threaten the firm to pay the ransom. Here, the single-factor authentication mechanism was further exploited by the attackers to gain access to Colonial’s IT network and, its sensitive data.
Hence implementation of multi-factor authentication is vital for the security of a firm’s critical infrastructure. Given that, password storage and maintenance and IAM (Identity and Access Management) is another key aspect of organizational security. Companies should mandate the use of a secure password management tool/platform to secure their critical infrastructure as a whole. This will ensure that there is no single sign-in and the owner/users of the account are informed when someone tries to log in with their password and user-id. Unauthorized privilege escalation can be prevented. One popular and secure password manager is 1Password.
Capital allocation to cybersecurity
Colonial testified that they allocate 200 million USD as IT investment, but the exact share of cybersecurity capital is not known. If organizations make an optimized investment in cybersecurity, the severity, as well as the likelihood can be reduced to a large extent.
Although Omdia’s ICT Enterprise Insights 2021 survey revealed that 60% of manufacturing companies are planning to increase investment in cybersecurity, which is promising, that still leaves another 40% quite vulnerable to disruption in their production aftermath of a cyber attack. An organization-centered security program assures faster incident response, recovery, and resilience.
Zero Trust Policy and Privilege Access Management
The zero-trust security policy implements user authentication for all users- internal or external, high or privileged. This assures the safety of the infrastructure even if the attacker tries to imitate a high privileged user. Also, a user must The picture depicts NIST 800-207 Zero-Trust framework.
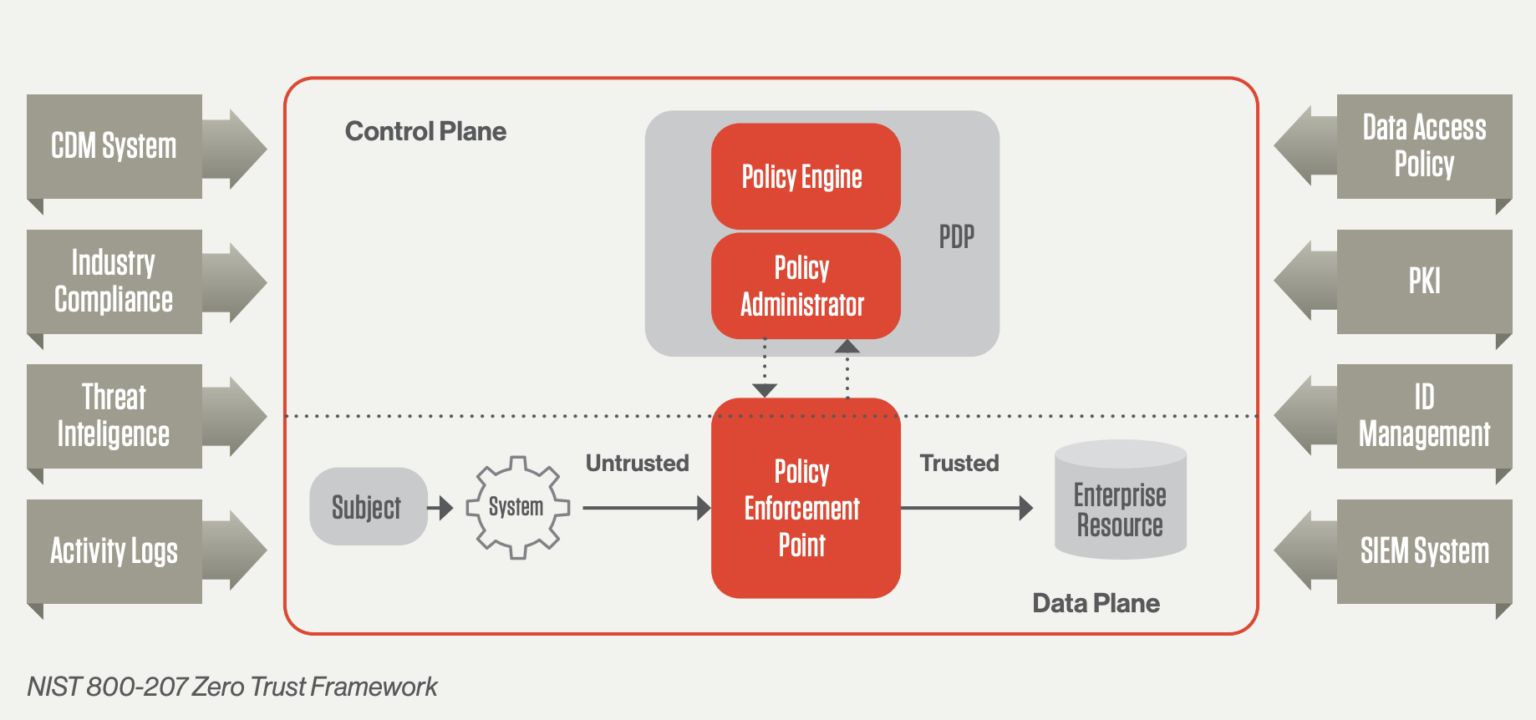
There is another policy that comes into play when different users have different privileges. The Principle of Least Privilege or PoLP is the principle where a certain user is given the minimum levels of access and permissions that are needed to perform the job. This principle guarantees that a certain user cannot exploit the functions above his privilege.
Resilient Security Structure: Incident response, Regular Backups and Incident Tracking
Once the attack or breach has occurred, the security structure must be strong enough to ensure that the organization gets to regular functioning reducing both financial and reputation losses. In the case of Colonial Pipeline, the working went down for several days resulting in gas panic-buying, shortages, and price spikes in some states. As the demand rose, the gas prices increased by six cents per gallon.
- A well-structured incident response will prevent any further damage to the infrastructure.
- Well-timed backups are important as they avoid the possibility of data losses.
- Incident Tracking mechanisms track the asset which was compromised by the attacker to gain access. This enables the security team to secure other similar assets thereby reducing the likelihood of a similar attack in the future.
The Human Factor: Importance of Cybersecurity Communities, Awareness and Education
Every cyber-attack comes down to one of the biggest threats to cybersecurity- the human factor. This encompasses not just the employees and the clients of an organization but also the general public. Cybersecurity awareness is an important aspect of a cyber-secure world. Security must be an individual initiative too- it should just not be the organizations and people working in the security community. There are various modes of cybersecurity awareness- Infosec communities, education programs, awareness initiatives, etc.
After the ransomware attack on the Colonial Pipeline, US President Joe Biden in his statement laid emphasis on training and equipping people with cybersecurity expertise. This will be done by greater investment in education to train and graduate more people proficient in cybersecurity.
Future cyber attacks can be prevented if nations take a greater interest in cybersecurity awareness and education. Organizations should encourage their employees to implement security best practices which in turn will make the organization more secure. Some steps to ensure individual security are:
- Use of password management tools,
- Avoiding the use of common or default passwords,
- Implement multi-factor authentication wherever possible,
- Using Email spam filters,
- Installation of the latest software and OS to avoid unpatched vulnerabilities,
- Use of good antivirus software and firewall.
These measures assure individual security that thereby improves the organization’s security or in the bigger picture, the nation’s security.